Have a look in the registry and see if you are receiving the following error:
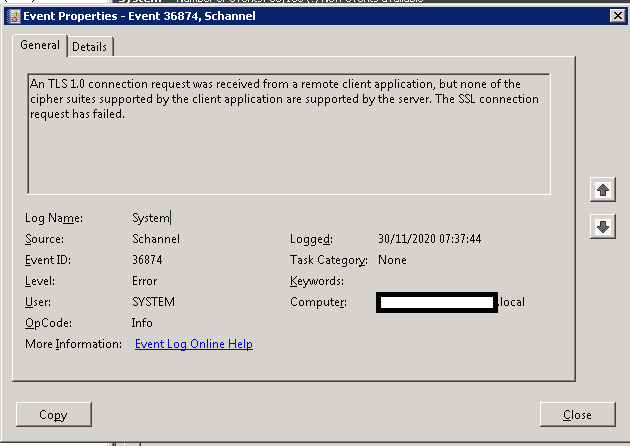
Log Name: System
Source: Schannel
Date: 30/11/2020 07:37:44
Event ID: 36874
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: site-DC1.domain.local
Description:
An TLS 1.0 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed.
Event Xml:
36874
0
2
0
0
0x8000000000000000
1379825
System
site-DC1.domain.local
TLS 1.0
As the inability of the Remote Desktop Gateway server to decrypt the TLS might explain the message.
You can resolve this easily by the following:
Open regedit on the Windows 2008 R2 server and navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Add
Keys called "
TLS 1.1" and "
TLS 1.2"
Under each of the two
keys you have just created, create two further
keys under each key called
Client and
Server Under each of those
keys, create
DWORD Values called:
DisabledByDefault [Value = 0]
Enabled [Value = 1]
Edited by user
4 years ago
|
Reason: Not specified
