This error indicates that there are AD users specified in the group policy for the Default Domain Controllers that can no longer be found in AD.
If you do [Windows] + R for RUN and enter RSOP.msc and run it you can see which Group Policies are creating this:
On the domain controller default policy it tends to be users added to the local policies\user rights assignment:
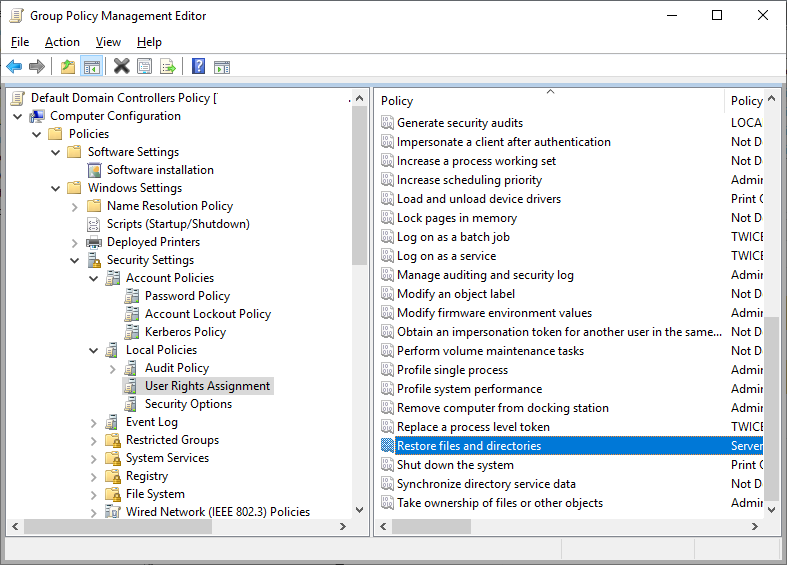
Once the non-existent users are removed, run GPUpdate and see if the error ceases.
Edited by user
4 years ago
|
Reason: Not specified
